Backupkeys
Can you recover my backup keys to get the flag , they probably are hardcoded ?
提示说明 flag 是硬编码;
进入IDA只有start和零散的几个函数,说明加壳了;
用16进制查看器搜UPX可以发现 UPX! 标志;
脱壳后看main函数:
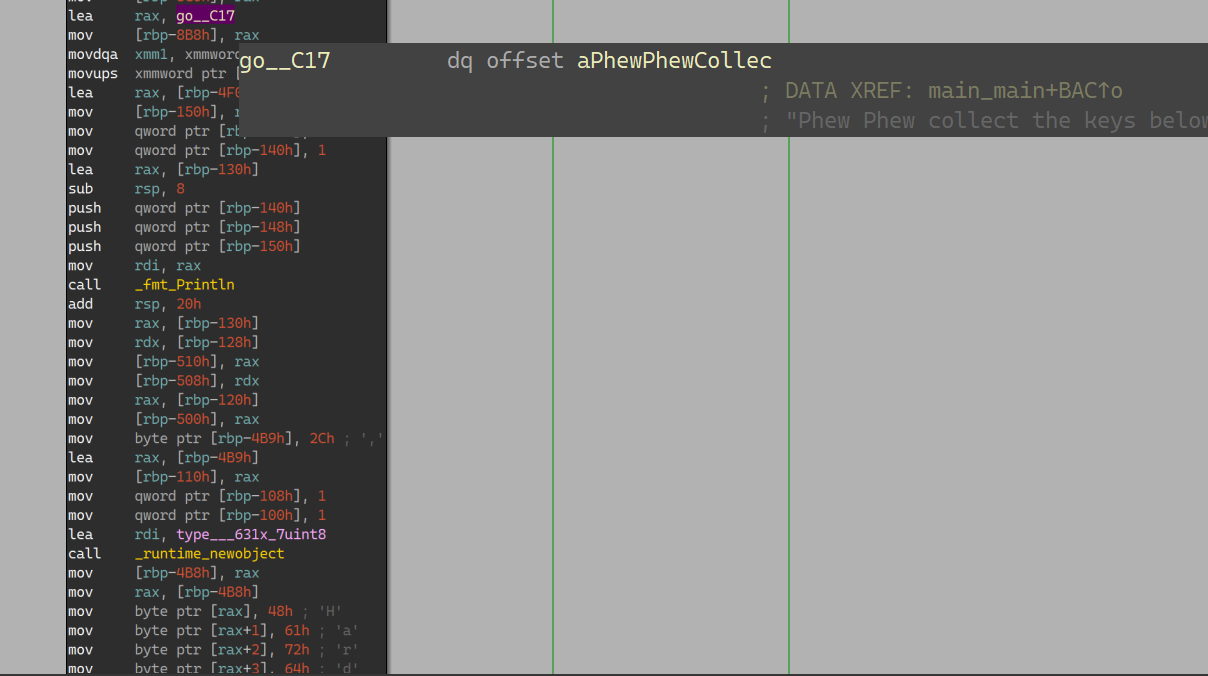
在最下方的输出 try harder的另一条线上有一个输出:
1 | "Phew Phew collect the keys below , don't forget to put them in flag{} format" |
消除逗号得到硬编码的flag:flag{Hardcodedpasswordsareuseless}
X-and-or
查看main:
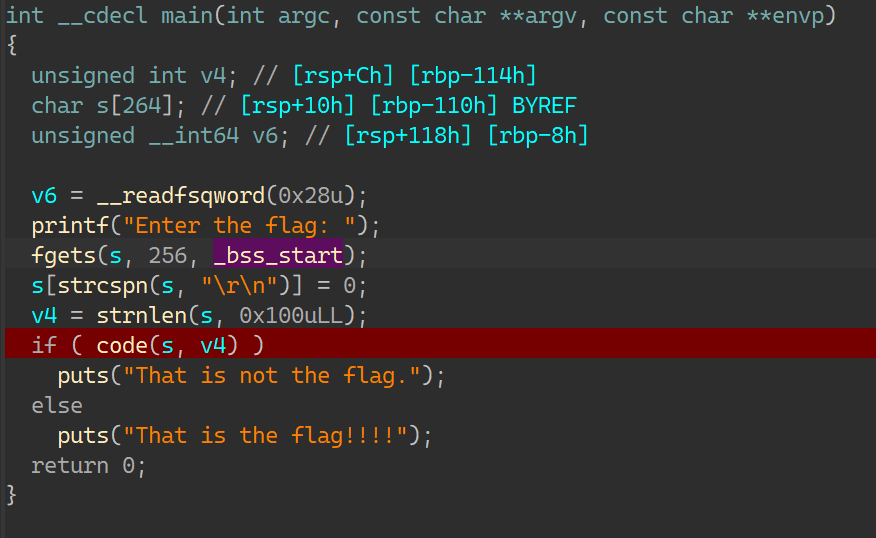
code是一个运行后设置的地址,跳转到主要函数;从code里的判断可得知,输入长度为38;进入运算后循环38次,内部有固定数字进行异或运算并与输入内容比较;
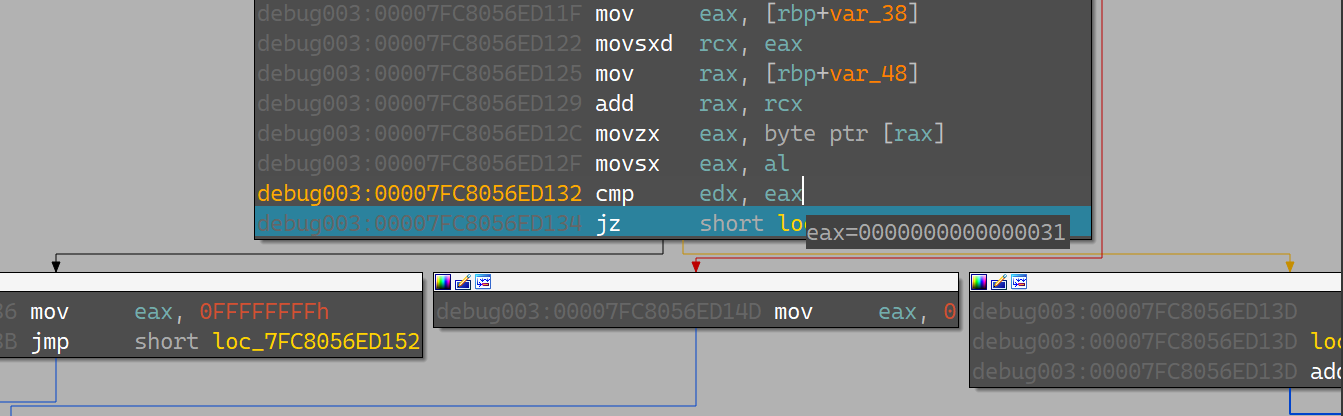
循环的结尾是比较数据,需要使得eax最终为0;经过调试可以发现每次异或0~5的立方,满6归0;
写出脚本:
1 | origin = [0x66, 0x6D, 0x69, 0x7C, 0x3B, 0x48, 0x36, 0x31, 0x3E, 0x28, 0x77, 0x19, 0x63, 0x31, 0x6C, 0x78, 0x24, 0x4E, 0x33, 0x63, 0x3D, 0x7D, 0x26, 0x4E, 0x37, 0x39, 0x30, 0x2B, 0x23, 0x1C, 0x31, 0x31, 0x6A, 0x29, 0x74, 0x1B, 0x62, 0x7C] |
由此得到flag:flag{560637dc0dcd33b5ff37880ca10b24fb}
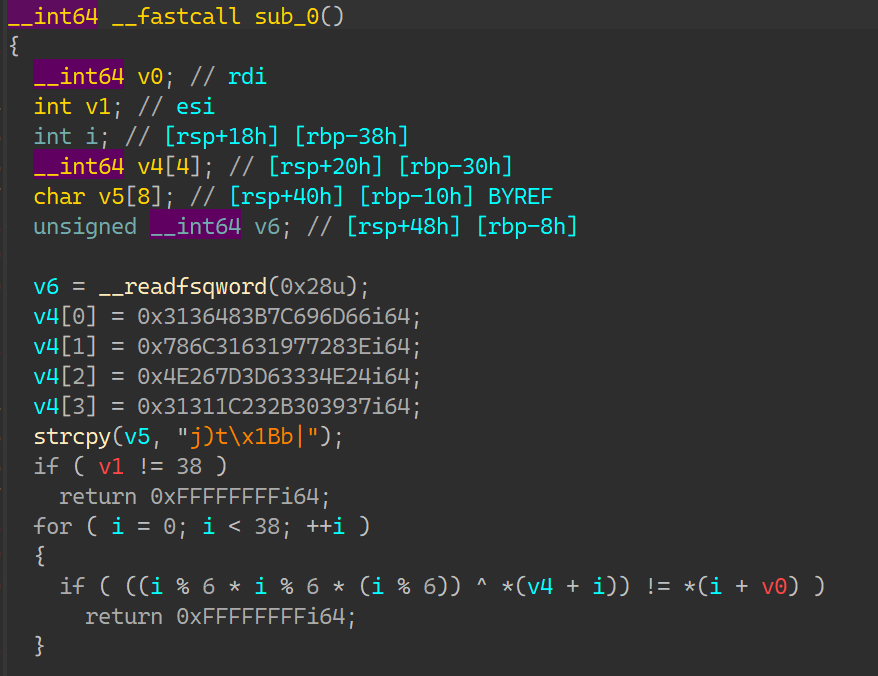
这题最有意思的是init函数,他把code的二进制内容异或上了0x42,需要将其变回来则再异或0x42,然后写在新的txt里,用IDA反编译,设置sp值,然后就能看到伪代码了:
Hash
I received a corrupted program the keys are probably lost within the game can you just find it for me to get the flag?.
Flag format : flag{key1+key2}
一开始看main觉得很奇怪,明明汇编有其他分支为什么伪代码始终显示的是 oops wrong path ?
结果发现是因为跳转的地方动了手脚:
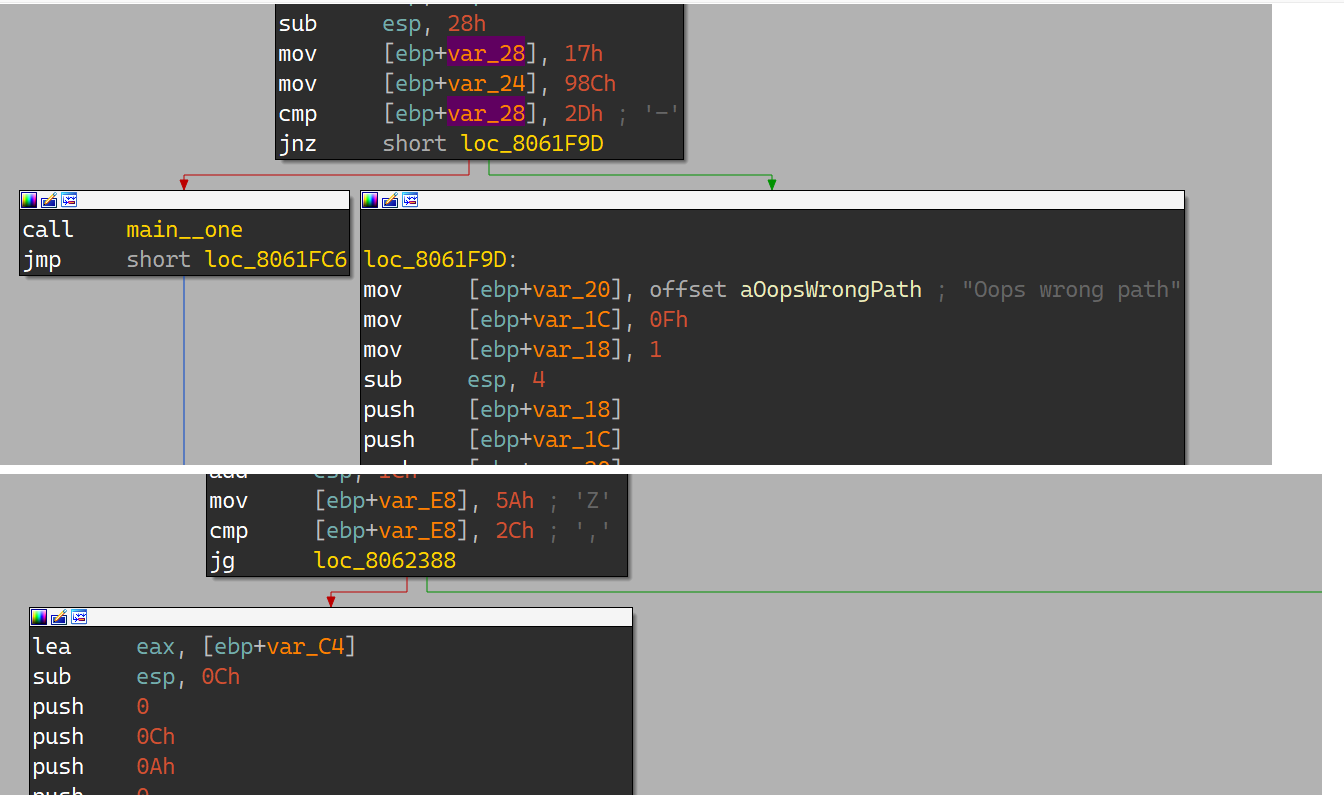
它始终都是判断必走另一条路,所以找不到正确的上下文;本来以为很难的题一下就变成了渣渣题;
里里外外都改一下jmp,再运行一遍,它就自己吐flag了;
得出:flag{456789JKLq59U1337}
Cage
Are you aware of the scopes yet?
开场patch main_one函数得到正确的上下文;
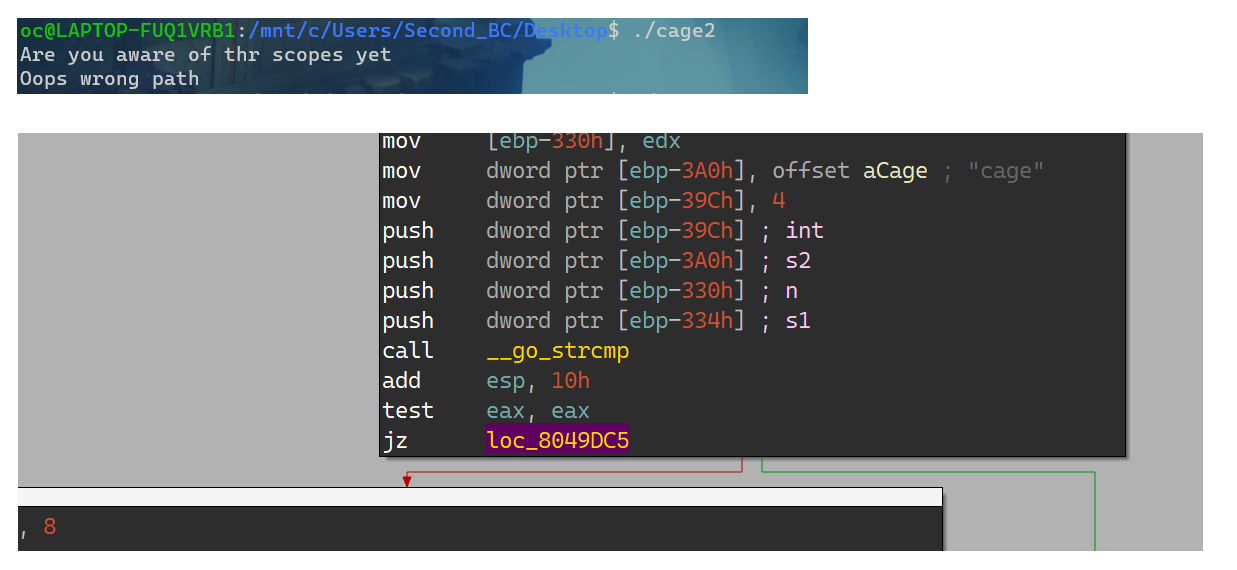
发现需要输入一系列magic code,然后它会吐出已有的字符串,直接将字符串拼起来得到flag:
flag{0xm4tr1xreal}
Ware
My plaintext has been encrypted by an innocent friend of mine while playing around cryptographic libraries, can you help me to recover the plaintext , remembers it’s just numbers and there’s a space between some numbers which you need to remove the space and submit the recovered plain text as a flag.
开始一个upx直接脱掉;
搜索运行时的字符串得到flag:flag{32117406899806798980909}
WrongDownload
My key has been missing inside these two binaries can you help me to find it out ,as per my friend the key is divided in two parts between the two binaries so, remember you need to join them up before submitting as a flag.
直接反编译就能找到:flag{S6c56bnXQiBjk9mqSYE7ykVQ7NzrRy}